
Products
FormsViewer: Design
FormsViewer is a provider hosted app (qfs.formsquo.com) implemented with a design similar to Microsoft Flow. There is a server piece which handles storage of form templates and authentication with cross-site applications that your forms may use. Form data is not stored on the server.
We store form templates (XSNs) on our Azure servers to facilitate unpacking their component parts (views, rules, data connections) for the client FormsViewer application which runs in the user’s browser via SharePoint Online.
FormsViewer servers run on Microsoft Azure in multiple locations to provide redundancy and responsiveness. We use Microsoft Azure security to prevent denial of service attacks, etc. Tokens for your site are not stored on the server. If you use the Manage Credentials feature in FormsViewer to query or submit to non-SharePoint sites, FormsViewer will store encrypted credentials for those third party services on the server. Most customers do not use this feature. No user information nor security credentials for your SharePoint site are stored on Qdabra servers.
Here is a diagram that describes the architecture:
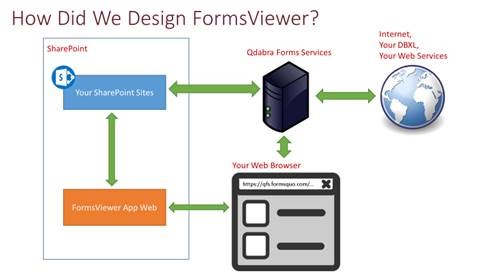
To summarize: rendering and processing of data is done in the browser on the user’s client machine (laptop, mobile device, etc.). The FormsViewer server is used to cache static form template components (XSL, XSF, PNG, etc.) for the browser app. The server may be used to query and submit connections with third party Web services but only if you have added data to the Manage Credentials page (and those credentials are encrypted). We do not store any form data, user information, or SharePoint credentials on our Azure servers, but the form templates (XSNs) are stored for caching static form template components for streaming down to the client browsers. Form templates describe form design (how the form looks, renders, and behaves). Form templates do not include content sensitive to organizations. Nevertheless, we do not provide access to your form templates to other organizations and use Azure security best practices to prevent unauthorized access to our servers.
